Every once in a while, someone asks me what I think of a given lock. The truth is, I am not a locksmith, I have barely had success at picking locks, and I am not a professional or even amateur penetration tester. What I do know is how to winnow down a selection process pretty quickly.
This is pretty much the thought process I use when evaluating locks, and the most-recent question had to do with a Schlage FE595 Keypad Entry Doorknob so you can follow along with me:
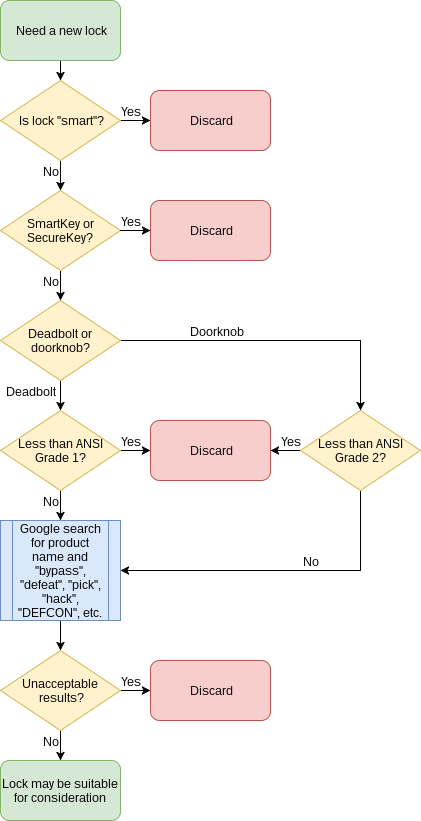
- Does the lock have “smart” functionality? If the answer is “yes”, I discard it immediately. The convenience of being able to lock/unlock your door over the internet or with your phone is undeniable, but companies treat electronic security as an afterthought, if at all. Time and time and time again, “smart” locks have proven to be massively vulnerable and companies’ responses have been far from inspiring, to the point that I am fairly sure that the ones presently claiming to be un-hackable simply have not been hacked yet. For the doorknob we are considering, it does have a keypad, but that exclusively operates the latch; it has no “smart” functionality at all.
- Is the lock a Kwikset SmartKey or Schlage SecureKey system? If the answer is “yes”, I discard it immediately. Both systems have known flaws, and the important thing to remember is that it does not matter what kind of high-tech wizardry surrounds them – if the cylinder of your lock is a SmartKey or SecureKey, that is the weakest point and it is very weak. In this case, while the lock was a Schlage, it does not have their rekeying functionality, so this is not a concern.
- Is the deadbolt at least ANSI Grade 1, or the doorknob at least ANSI Grade 2? Hopefully everyone remembers my explanation of what ANSI grading actually means, but given the relatively small increased cost of buying Grade 1 versus lower grades, I tend not to buy any lower grades. Schlage advertises this doorknob to be Grade 2, so we are good to go.
- What happens when you search for the product name and “bypass”, “defeat”, “pick”, “hack”, or “DEFCON”? Like I said, I was never an official intrusion tester; I always approached the problem from the other side of the equation, though we tried to do informal “red teaming” to determine our weaknesses ourselves. But there are a lot of highly-skilled individuals out there who pass the time by trying to break things and see what happens, and a lot of them attend an event called DEFCON – the world’s largest combined hacker / security conference since 1993. The good news is that most of these individuals are what are colloquially known as “white hats” or “ethical hackers” – if they find a weakness in a given security product, they let the company know and give the company a chance to correct it. The bad news is that not every company takes advantage of that opportunity (see: Kwikset). Unfortunately, while executing those searches on our example lock, the following videos floated to the surface:
… and …
Not only can the lock core be pick-gunned, but a single, small hole in a specific, unobtrusive location is all that it takes to have complete control over the doorknob for the remainder of its existence.
As for what constitutes a “fatal flaw” for a lock, that is something you are going to have to decide. Susceptibility to pick-guns is a pretty significant problem, but knowing to drill a hole in a specific spot and stick a piece of metal in it a specific way? It all depends on how intelligent and educated you believe your potential attackers will be.
And that is pretty much my “first pass” test sequence. It is important to note, and I cannot stress this enough, that just because a lock made it through the process does NOT mean it is a secure lock. As the saying goes, absence of evidence is not evidence of absence, and not finding anyone demonstrating a vulnerability on the lock merely means that no one has demonstrated a vulnerability yet. It does not mean there are no vulnerabilities.
However, these simple steps will cull out those many, many locks that manufacturers are still selling despite known flaws in their designs.

Thanks for another entertaining and informative post, Jon! I got a pretty good laugh out of that Securekey video and the firefighter forced entry training videos a few weeks back.
Yeah, the SmartKey flaw at least requires actual damage to the lock – invisible damage, but still. The SecureKey situation blew me away.
When you get the time, watch some more of Mr. Locksmith’s YouTube; he’s as honest as he is educated in the trade, and has no problems calling out flaws.
[…] understand the appeal and convenience, but I will remind you of the flowchart I posted a while ago regarding lock selection – the very first gate is whether or not the locks are “smart”. Now, security […]
[…] a conversation with a friend, it occurs to me I need to update / clarify my lock selection process flowchart, specifically concerning the “unacceptable results” […]